Platform Engineering on Proxmox with CAPMOX and Sveltos
Summary:
Learn how to use Sveltos to automate the creation of Cluster API (CAPI) clusters on Proxmox using the CAPMOX provider.
Cilium provides eBPF-based networking, security, and observability for cloud-native environments like Kubernetes, offering advanced traffic management and policy enforcement.
View All TagsSummary:
Learn how to use Sveltos to automate the creation of Cluster API (CAPI) clusters on Proxmox using the CAPMOX provider.
Summary:
We continue where we left off with the CAPMOX deployment. In this post, we will go through common issues during deployment and the tools used to troubleshoot and resolve them.
Summary:
Learn how to use the image-builder to craft a base Ubuntu 24.04 image for Kubernetes and how Cluster API (CAPI) helps teams provision, manage, and automate the lifecycle of Kubernetes clusters on a Proxmox server.
Summary:
Talos Linux Kubernetes module updates for ongoing operations.
Summary:
An easy way to migrate ArgoCD running on an RKE2 cluster from Ingress NGINX to Cilium Ingress.
Summary:
This is part 3 of the step-by-step guide to creating Kubernetes managed clusters on Azure Cloud using Cluster API (CAPI) and Sveltos! We will give platform teams and seasonal engineers a simple, secure, and flexible way to build Kubernetes clusters.
Summary:
This is part 2 of our series. Here, we show how to use Cluster API (CAPI) to create Azure Kubernetes managed clusters. We’ll use Cilium as our Container Network Interface (CNI) and explore additional features. Follow along to experiment with CAPI and explore the Azure cloud.
Summary:
In this post, we show how to use Cluster API (CAPI) to create Azure Kubernetes managed clusters. We will use Cilium as our Container Network Interface (CNI) and explore additional features. Follow along to experiment with CAPI and explore the Azure cloud.
Summary:
Learn how to integrate Cilium, Gateway API, cert-manager, let's encrypt and Cloudflare to dynamically provision TLS certificates for ArgoCD.
Welcome to part 4 of the dual-stack series! In parts 1, 2, and 3, we walked through how to set up dual-stack networking on a Proxmox server using our Internet provider. We also showed you how to deploy RKE2 Kubernetes clusters and share both IPv4 and IPv6 services across them. Now, in the final part of the series, we are diving into some of the most commonly used features of Cilium for a home lab setup! Let’s get started!

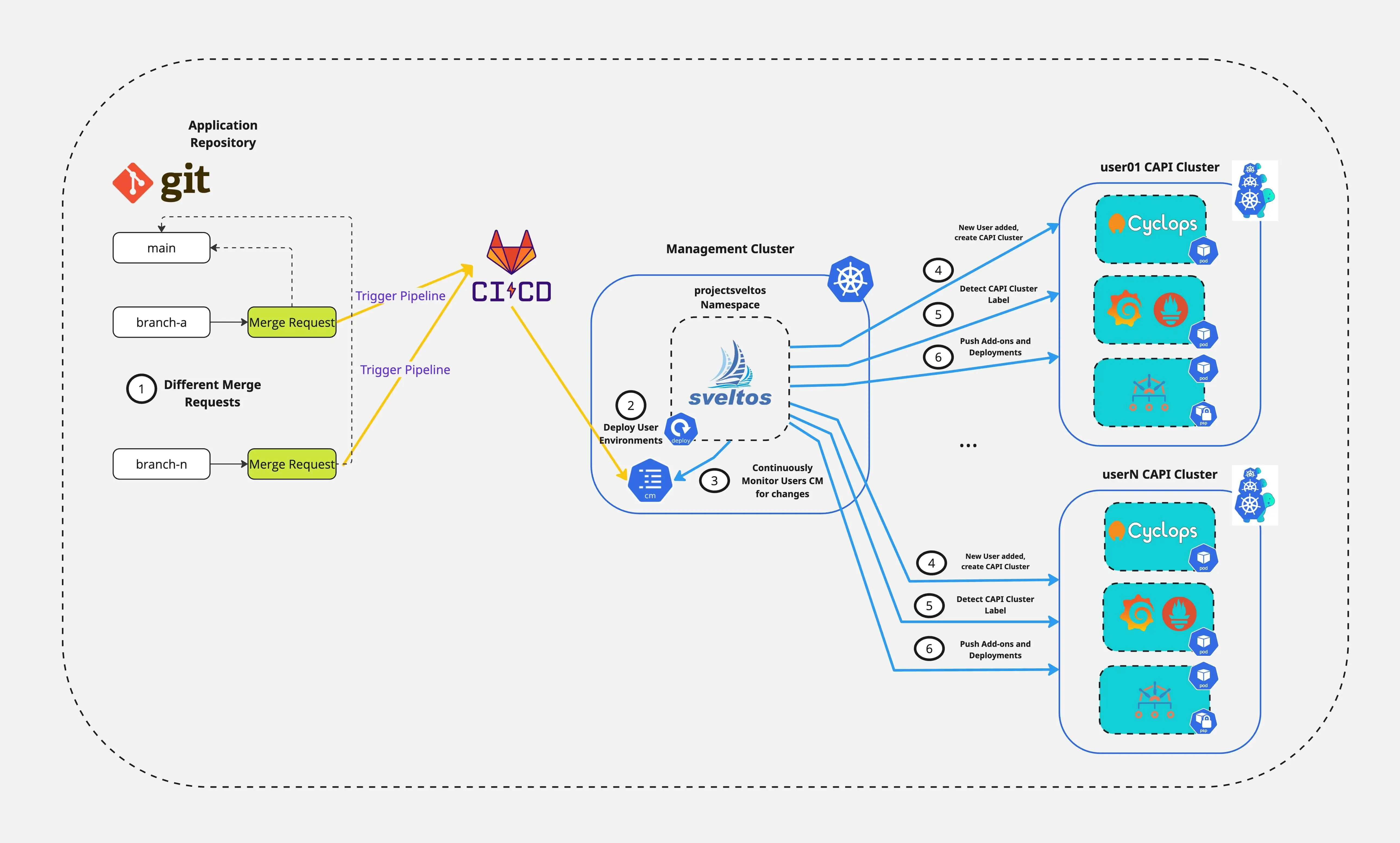
Are you ready to simplify how your Platform team spins up and down development environments while improving DevX? In this post, we show how Cluster API(CAPI), Sveltos, and Cyclops work together. They automatically create Kubernetes environments. This setup lets developers easily interact with and manage their applications. It is not magic, it is the power of Sveltos combined with the right tooling!
Welcome to part 3 of the dual-stack series! In part 1 and part 2, we discovered how to enable dual-stack on a Proxmox server using our Internet provider and deploy RKE2 clusters. In today's post, we continue our journey and enable a Cilium Cluster Mesh between two RKE2 clusters. The goal is to share IPv4 and IPv6 services between the different clusters effortlessly. Let’s dive in!
Welcome to part 2 of the dual-stack series! In part 1, we covered how to enable IPv6 Prefix allocation using pfsense on Proxmox with Fritz!Box as a home router. The setup allows virtual machines in a dedicated interface to receive an IPv4 and an IPv6 address. If you have completed part 1, you can continue with the dual-stack RKE2 setup powered by Cilium.

Welcome to part 3 of the Talos Linux Kubernetes cluster bootstrap of the Proxmox series. In today's post, we will perform changes to make the code reusable and extensible. Users can follow a GitOps approach towards Talos deployments.
We assume you already have the basic project structure. To follow along, check out part 1 and part 2 posts.

Welcome to part 2 of the Talos Linux Kubernetes cluster bootstrap on the Proxmox series.
We will enable Cilium as our CNI (Container Network Interface), use KubeProxy replacement, and set up Cilium Hubble for network observability. We will outline basic kubectl commands to evaluate the Cilium setup alongside network tests.
We assume you already have the basic project structurefrom part 1, as we will extend the configuration for Cilium. To follow along, check out the part 1 post.

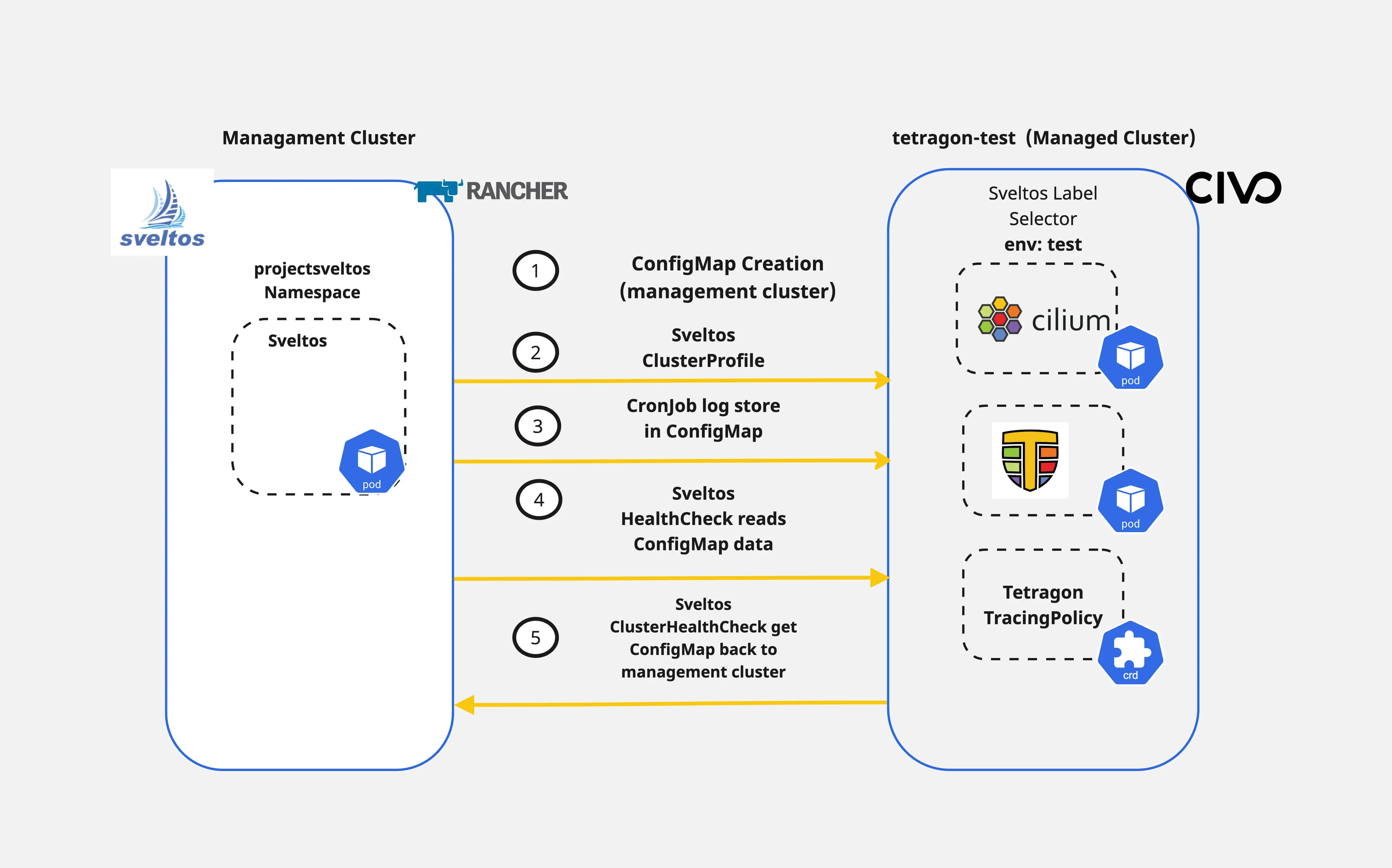
How easy is it to handle Day-2 operations with existing CI/CD tooling? Sveltos provides the ability to perform not only Day-1 operations but also helps platform administrators, tenant administrators and other operators with Day-2 operations. For example, we can use the HealthCheck and the ClusterHealthCheck features to not only watch the health of a cluster but also collect information from the managed clusters and display them in the management cluster.
In today's blog post, we will cover a way of deploying Cilium as our CNI alongside Cilium Tetragon for observability. We will then continue with a simple TracingPolicy deployment to capture socket connections and then use Sveltos to display the tracing results back to the management cluster.
The goal of the demonstration is to showcase how Sveltos can be used for different Kubernetes cluster operations based on the use case at hand.
In a previous post, we covered how to create an RKE2 cluster on Azure Cloud using the cloud-free credits from the Rancher UI. As this is a convenient approach to get started with Rancher, in today's post, we will demonstrate how to use OpenTofu to automate the deployment.
OpenTofu is a fork of Terraform. It is an open-source project, community-driven, and managed by the Linux Foundation. If you want to get familiar with what OpenTofu is and how to get started, check out the link here.
We will also show how easy it is to customise the Cilium configuration. Plus, we will enable kube-vip for LoadBalancer services using HCL (HashiCorp Configuration Language).

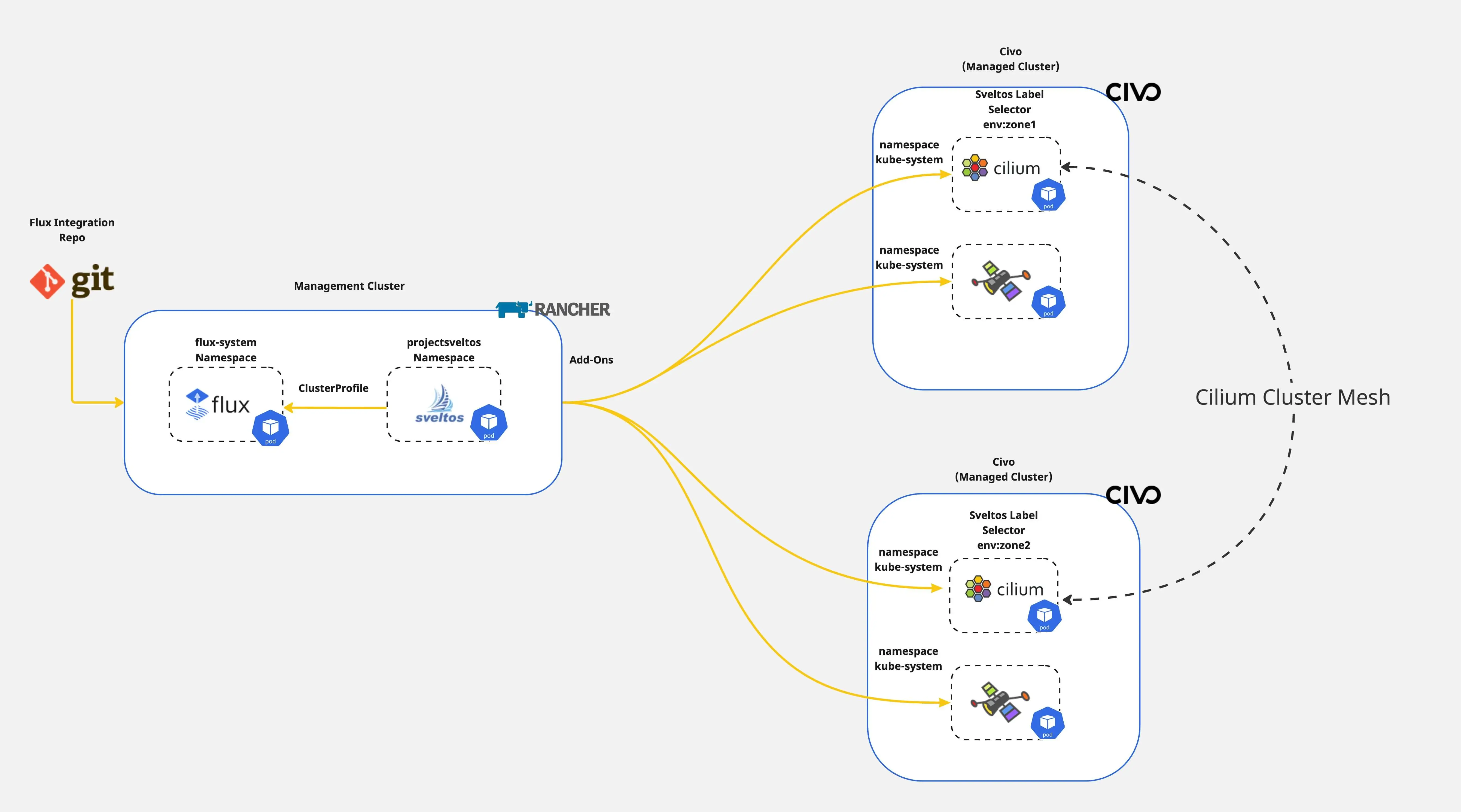
Have you ever wondered how to dynamically instantiate Kubernetes resources before deploying them to a cluster? What if I tell you there is an easy way to do it? Sveltos lets you define add-ons and applications using templates. Before deploying any resource down the managed clusters, Sveltos instantiates the templates using information gathered from the management cluster.
In a previous post, we outlined a step-by-step approach to forming a Cilium cluster mesh between two clusters. In today's post, we will demonstrate how the Sveltos templating is used to deploy a Cilium cluster mesh dynamically in one go.
For the last couple of days, I have been working on a new use case installing RKE2 clusters powered with Cilium by Azure Cloud. The requirement at hand was to use a Rancher instance and from there start deploying RKE2 clusters. I found that the official Rancher documentation has outdated instructions for pre-configuring Azure Cloud.
In today's blog post, we will outline the steps to set up Azure cloud-free credits for deploying RKE2 clusters with Cilium. Additionally, we will cover any limitations that come with the free credit concept.

Working with on-prem RKE2 clusters, I noticed many issues in forming a Cilium cluster mesh between clusters in an automated way.
In this post, I will walk through a step-by-step process to get a Cilium cluster mesh up and running. We will cover the problems I ran into along the way. The goal is to follow a GitOps-friendly approach, with no need for the Cilium CLI. We will use Helm and kubectl for the setup.